Install FreeRADIUS & daloRADIUS on CentOS 8 + MySQL/MariaDB
FreeRADIUS is an open-source, scalable, modular, and high-performance RADIUS protocol server. FreeRADIUS is in fact the most popular and widely deployed RADIUS server.
It’s used mainly to perform AAA i.e. Authorisation, Authentication, Accounting services on various types of network access.
It works as a daemon on UNIX and UNIX-like operating systems.
The FreeRADIUS server connects and talks with a client including Ethernet switches, Wireless access points, terminal servers, or a PC configured with the appropriate software (radiusclient, PortSlave, etc).
In this article, we’ll explain the step-by-step process of installing FreeRADIUS and DaloRADIUS on CentOS 8 with MySQL or MariaDB.
Prerequisites
- A server running CentOS 8
- We recommend acting as a non-root sudo user. This is because if you are logged in as root you can easily destroy your system if you’re not careful.
We will be using DNF (Dandified YUM) instead of YUM. DNF is the default package manager for Fedora 22, CentOS 8, and RHEL 8 distributions. DNF is the next-generation version intended to replace yum in RPM-based systems. It’s a powerful package manager and capable of automatically resolving dependency issues.
Update package index:
Video Version of this Tutorial
We’ve also included the video version of this tutorial, where go through it from start to finish. This may help in case there’s situations where the writing seems unclear and it’s easier to follow by watching us go through the steps.
Install LAMP Stack on CentOS 8
LAMP stack is a set of open-source softwares that can be used to create web applications and websites. LAMP stands for its original components Linux, Apache, MySQL, PHP. The LAMP stack is no longer limited to the original open-source components.
Install Apache Web Server
Install the httpd package:
Press Y and ENTER if prompted.
Start Apache and enable it so it starts on boot:
If you have firewall enabled, we need to enable HTTP connections to Apache:
Reload it to apply the changes:
Check if Apache is running by visiting your server’s IP address (with HTTP, not HTTPS), you should see something like this:
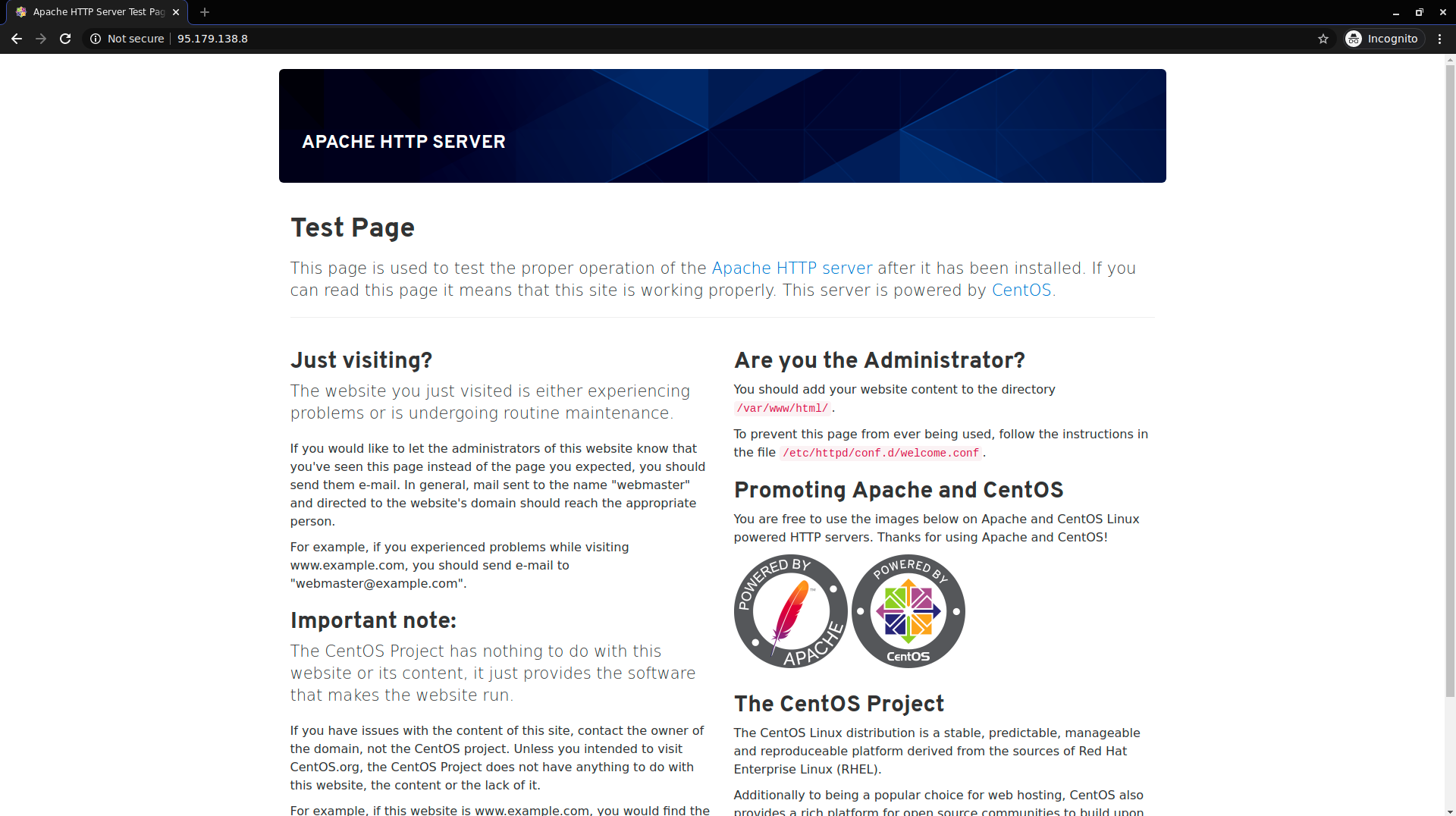
Make sure to visit http://your_ip and not https://your_ip. If you get an error check the address you’re visiting, because your browser might have added https:// instead of http://
Install MySQL / MariaDB
Now we’ll run a script that MariaDB ships with, which takes us through some steps to improve our MariaDB security options:
You’ll be taken through a series of prompts. We recommend you fill them out as follows:
Unless you know you set a password, just press enter when prompted:
Next confirm that you want to set a new root password and set a strong password:
Next you can just press ENTER for the prompts that follow (unless you have other plans in mind that we don’t cover in this tutorial).
Remove anonymous users:
Disallow root login remotely:
Remove test database:
Reload privilege tables:
Now MariaDB (or MySQL) should be successfully set up on your machine.
Install PHP
Install PHP 7.3 / PHP 7.4 on CentOS 8 (Optional)
The default version distributed with CentOS 8 is PHP7.2. If you want to install PHP 7.2, then you can skip this step.
Enable the Remi Repository
Install PHP 7.3
Install PHP 7.4
// chọn 1 trong 2 phiên bản php để cài đặt thôi nhé
Enable the PowerTools repository, as some packages may depend on some of its packages:
Install PHP and some popular PHP extensions:
If you also intend to install daloRADIUS, the freeRADIUS GUI, you’ll also need to install PEAR, a PHP extension, from which we’ll install some dependencies.
Next we install the DB and MDB2 libraries from the PEAR repository. These are required by daloRADIUS to work.
Install freeRADIUS and Configure with MySQL/MariaDB on CentOS 8
Install FreeRADIUS
Use the dnf module list command to list the modules available to our system related to freeradius.
You should see something like this:
Install the FreeRADIUS module, FreeRADIUS client utilities, and the MySQL module for FreeRADIUS.
Start the RADIUS service:
Check the status of the service to make sure it’s active and there are no issues so far:
Example output:
Configure CentOS 8 Firewall for FreeRADIUS
We’ll need to configure Firewalld to allow radius packets.
RADIUS uses ports 1812 for authentication and port 1813 for accounting, so we’ll need to allow traffic on these ports. Upon installing FreeRADIUS, it added it’s configuration to firewalld, so to allow radius traffic in and out run the following command:
Reload the firewall for changes to take effect:
You can check the configuration file added by FreeRADIUS to Firewalld by running:
Example output:
Confirm that the changes have been successfully added to the default zone. The services we mainly want to see are http, https, and radius.
The services we allowed so far in this guide (http, https, and radius) are listed in the output, so we can proceed.
Test the RADIUS Server
To test that FreeRADIUS works we’ll run it in debug mode. To do this we’ll first have to stop the current running process. If we run it in debug mode while the other process is still running, then we’ll get an error.
To stop the current process stop the service by running:
Run the RADIUS server in debug mode:
You should get an output ending in:
If the output looks good then stop debug mode by pressing Ctrl+C, and start the service again by running:
Configure freeRADIUS to use MySQL/MariaDB
Now we’ll configure MySQL/MariaDB for FreeRADIUS.
First we’ll create a database and a database user for FreeRADIUS, then create a database, and a user identified by a password.
In this example we’ll use the following details:
Database: radius
User: radius
Password: Somestrongpassword_321
You can replace the names and password with whatever you like, but you’ll have to pay attention in configurations we’ll do later on, to appropriately replace values.
Start by accessing the MySQL/MariaDB console as root:
Run the commands to create the database and user:
Next import the RADIUS MySQL schema into the newly created database:
Create a soft link for SQL under /etc/raddb/mods-enabled/
Now we’ll configure FreeRADIUS to use MySQL. We do this by editing the file /etc/raddb/mods-available/sql. You can use your favorite text editor. I’ll install and use nano:
The file is long, due explanations and lines that are commented out, but we’ll just edit a few lines:
- Change driver = "rlm_sql_null" to driver = "rlm_sql_mysql"
- Change dialect = "sqlite" to dialect = "mysql"
- When configuring FreeRADIUS to work with MySQL, we’ll find that the
MySQL configuration assumes we’ll use TLS by default. For the purposes
of this tutorial we won’t be using SSL certificates, so we will comment
out the TLS section. To do this we’ll have to find this section in the
file and comment it out. Here it is in its initial state:
mysql {# If any of the files below are set, TLS encryption is enabledtls {ca_file = "/etc/ssl/certs/my_ca.crt"ca_path = "/etc/ssl/certs/"certificate_file = "/etc/ssl/certs/private/client.crt"private_key_file = "/etc/ssl/certs/private/client.key"cipher = "DHE-RSA-AES256-SHA:AES128-SHA"tls_required = yestls_check_cert = notls_check_cert_cn = no}# If yes, (or auto and libmysqlclient reports warnings are# available), will retrieve and log additional warnings from# the server if an error has occured. Defaults to 'auto'warnings = auto}
And this is how it looks with the tls section commented out:
mysql {# If any of the files below are set, TLS encryption is enabled# tls {# ca_file = "/etc/ssl/certs/my_ca.crt"# ca_path = "/etc/ssl/certs/"# certificate_file = "/etc/ssl/certs/private/client.crt"# private_key_file = "/etc/ssl/certs/private/client.key"# cipher = "DHE-RSA-AES256-SHA:AES128-SHA"# tls_required = yes# tls_check_cert = no# tls_check_cert_cn = no#}# If yes, (or auto and libmysqlclient reports warnings are# available), will retrieve and log additional warnings from# the server if an error has occured. Defaults to 'auto'warnings = auto}// Đoạn này chúng ta thêm dấu # trước đầu dòng để chuyển thành ghi chú , chỉ để lại giá trị warnings=auto - Uncomment server, port, login, and password, and also change some of their values.They initially look like this:
# Connection info:## server = "localhost"# port = 3306# login = "radius"# password = "radpass"# Database table configuration for everything except Oracleradius_db = "radius"
Change them by uncommenting them and changing their values to correspond to the database and user you created earlier:
//Thay đổi các giá trị sau bằng cách bỏ dấu # trước dòng và gõ lại thông số:
# Connection info:#server = "localhost"port = 3306login = "radius"password = "Somestrongpassword_321"# Database table configuration for everything except Oracleradius_db = "radius" - Uncomment the line containing by removing the # symbol at the beginning of the line read_clients = yes
- Save the file. If you’re using nano then press Ctrl+XandENTERto save the file and exit.
Nếu sử dụng Vim/ vi thì nhấn :x để lưu lại
Now change the group rights of the file we just edited to radiusd:
And restart the radiusd service:
Since we’ve made significant changes, we’ll test again in debug mode to make sure FreeRADIUS is working.
Stop the radiusd service:
And run it in debug mode:
You should get a long output ending in something like:
Now FreeRADIUS is installed and working with MySQL or MariaDB on your CentOS 8 server.
The following steps are to install daloRADIUS, a FreeRADIUS web panel. As such, these are optional, and only if you want to use the web panel.
Install & Configure daloRADIUS (FreeRADIUS GUI) on CentOS 8 (Optional)
daloRADIUS is an advanced RADIUS web management application. It’s aimed at managing hotspots and general-purpose ISP deployments. It offers multiple excellent features like a powerful graphic interface, advanced user management, billing engine, integration with Google Maps, and more.
Install wget
Download the daloRADIUS from Github:
Install unzip if you don’t already have it, unzip the daloRADIUS archive, and move it into the DocumentRoot.
Nếu chưa cài đặt zip thì cài ở bước này để có thể dùng Unzip
#yum install zip Document root file is the folder where website files for a specific domain are stored. It’s important to have a unique folder for each domain as cPanel allows for multiple domains (subdomains and add-on domains).
After installation of Apache, the document root file is located at the /var/www/html/
by default but we can change the location of the directory later.Navigate via cd in the daloradius folder /var/www/html/daloradius so we can easily import daloRADIUS MySQL tables:
Now change the ownership of the daloradius folder to the Apache webserver.
Next we’ll need to create our daloRADIUS configuration file. We’re provided with a sample of such a configuration file, that we’ll need to copy and change it’s name. The sample file is called /var/www/html/daloradius/library/daloradius.conf.php.sample and to create the file we’ll run the following command to copy and rename it:
And we’ll also make the daloradius.conf.php configuration file writable by the webserver.
Open the daloradius.conf.php configuration file so we can edit MySQL information:
Change the values to your database user/password/database name:
Press Ctrl+X and ENTER to save and exit, if you’re using nano to edit the file.
Restart the radiusd service and check it’s status to make sure it’s working.
By default, CentOS 8 has SELinux enabled and in enforcing mode.
SELinux (Security-Enhanced Linux) is a Linux Kernel security module. It gives administrators more control over who can access the system. It was first introduced in CentOS 4 and improved in the later CentOS versions.
We’ll have to make changes to the SELinux policy to allow apache user access, and we’ll do this using the semanage command.
SEmanage is used to configure certain elements of SELinux policy without modifying or recompiling the policy resources. Semanage command can be used to adjust port context, file context, and booleans.
This allows us to browse the existing default context policies and create our own policies.
To enable the semanage command, we’ll install SELinux Policy Core Python Utilities, which contains semanage.
You might face problems in deploying web applications on CentOS while not using the default Apache directories (for content or log). We can create custom policies to apply the proper SELinux context types to your files and directories. This will give you independence in the placement of your application files.
This will protect you if (for some reason) your context settings disappear. You can quickly solve the problem by running a context restore to get your application running again in no time!
Now we’ll create and apply the policy to allow Apache to read and write daloRADIUS files:
Now daloRADIUS should be installed and working.
To access it visit http://your_server_ip_or_domain/daloradius. If you get an error then check to see if your browser changed http:// into https:// and change it back.
// Đăng nhập vào daloradius bằng password mặc định là: Administrator/radius , sau đó tiến hành đổi mật khẩu.
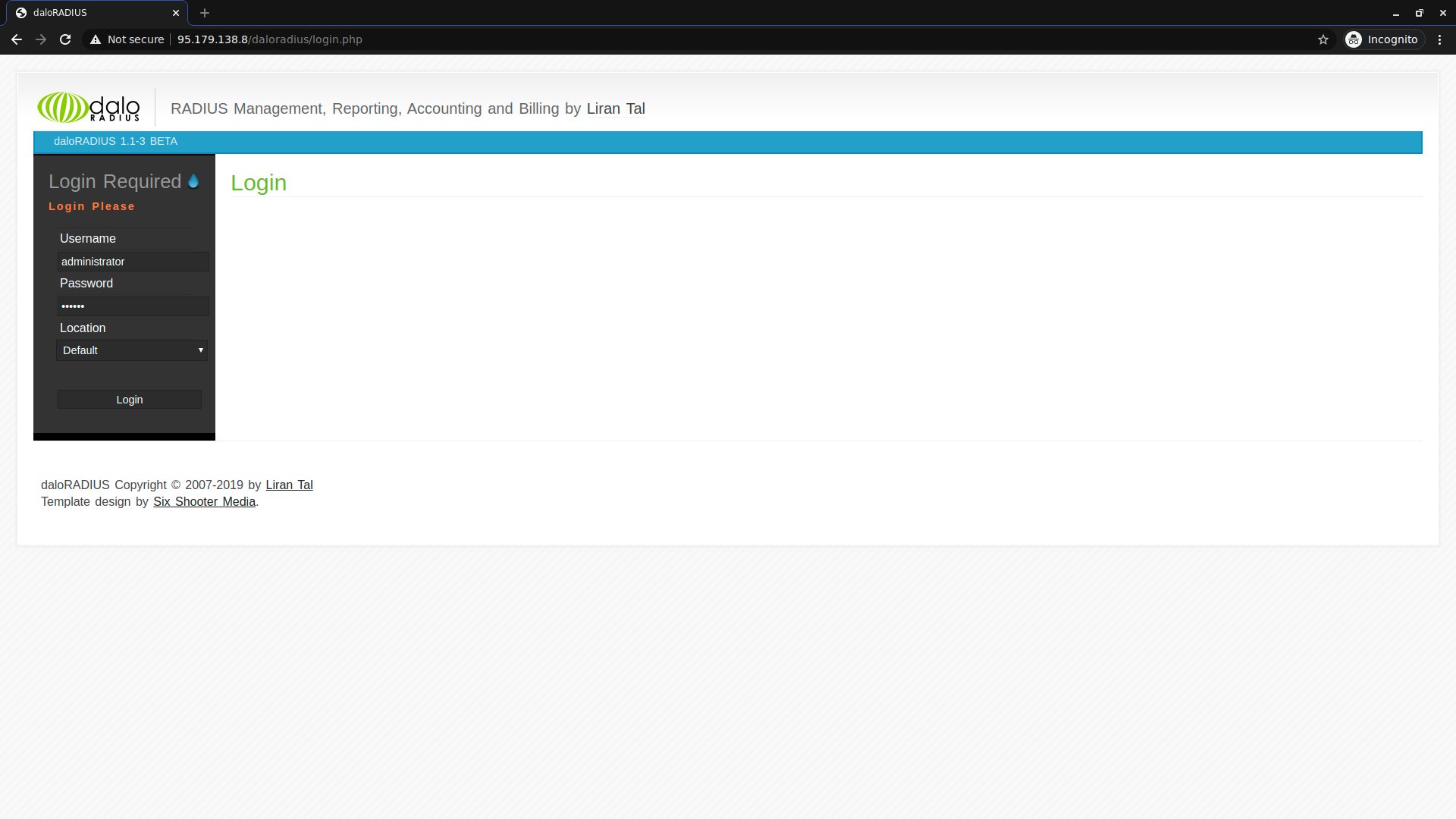
Change daloRADIUS Administrator Password
Having a default login like administrator/password is a security vulnerability for anyone scanning for servers with daloRADIUS installed, so you’ll want to change you’ll want to at least change your password right away.
You can change it by logging into daloRADIUS > Config (In the top menu) > Operators (In the submenu) > List Operators (In the gray sidebar) > Click on administrator and in the next screen change the password and click Apply.
Testing daloRADIUS Web Panel
To test that FreeRADIUS and daloRADIUS are working, we’ll perform some basic operations in daloRADIUS and then send a test Authentication Request from another computer to our FreeRADIUS server.
1. Creating a NAS Client Table
The Network Access Server (NAS) client table acts as a gateway that guards a protected resource. For another computer to connect to our RADIUS server, it needs to be added to the NAS client table.
The NAS is an intermediary that a client connects to, then the NAS asks the resource (in our case the RADIUS server) if the credentials are valid, and based on this the NAS will allow or disallow access to the protected resource.
You can read a bit more about the NAS on this page from the FreeRADIUS wiki.
To create the NAS table, in the top menu navigate to Management, and in the submenu click on Nas. Then in the left sidebar click New NAS.
You’ll have to fill in the following:
NAS IP/Host: the IP or fully qualified hostname from which you’re trying to connect
NAS Secret: a password for connecting to the NAS, but it’s referred to as a secret. It’s used to communicate between the client/NAS and RADIUS server.
NAS Type: There are a few types that are recognized,
including livingston, cisco, portslave. This is passed to the external
checklogin program when it is called to detect double logins. For the
purposes of this tutorial we’ll go for
NAS Shortname: An alias that can be used in place of the IP address or fully qualified hostname provided under NAS IP/Host
For our example we’ll fill in:
NAS IP/Host: IP of another computer we’re using as a client
NAS Secret:
NAS Type:
NAS Shortname:
2. Create a User
To create a user navigate in the top menu to Management, in the submenu Users, and next in the left sidebar New User.
We’ll just fill in Username and Password and leave the Password Type and Group as they are.
For our example we’ll fill in:
Username:new_customer
Password: customer_strong_passwd_123
There are more attributes to configure, but for the purpose of this tutorial we’re filling in basic info to get FreeRADIUS set up and working.
Now we can test our NAS table and user.
Important Note
Every time a NAS is added you need to restart FreeRADIUS so it fetches the updated table.
To test FreeRADIUS we’ll run it in debug mode so we can see the output when we try to connect with our newly created user.
The service is probably still running normally, so we’ll first stop it and then run it in debug mode as we’ve done when we first tested it:
Stop the radiusd service:
And run it in debug mode:
The output should be something like this:
" 3. Test with NTRadPing
For convenience, we’ll test the server using a free software for Windows, called NTRadPing.
You can download it here https://community.microfocus.com/t5/OES-Tips-Information/NTRadPing-1-5-RADIUS-Test-Utility/ta-p/1777768. This is a direct link to the archive https://community.microfocus.com/dcvta86296/attachments/dcvta86296/OES_Tips/148/1/ntradping.zip
To run it just unzip the archive and run the executable.
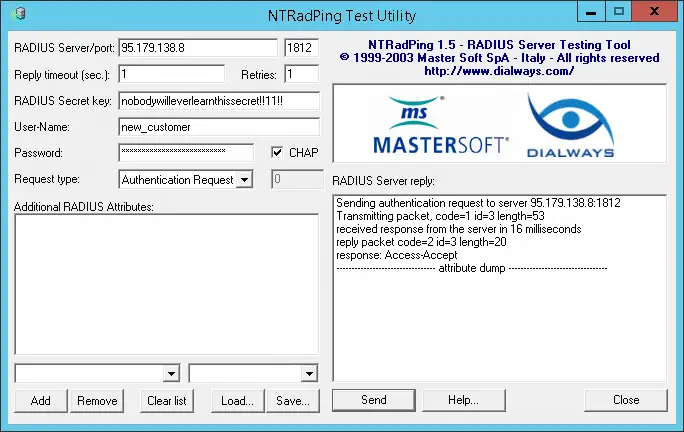
This is how it looks like and how we’ll fill in the details in NTRadPing. We’ll use it to send an Authentication Request to the RADIUS server while it’s running in debug mode, so we can see first hand how it accepts the request.
We’ve filled the fields as follows:
RADIUS Server/port: IP of the server we have FreeRADIUS installed on / port
Reply timeout (sec.):
Retries:
RADIUS Secret key:
User-Name:
Password:
Lastly check the
Now you can test the RADIUS server. Just click Send in NTRadPing and if you get an
The output should look something like this:
Conclusion
Well done. You’ve set up FreeRADIUS, configured it to use MySQL or MariaDB, along with daloRADIUS, on a CentOS 8 server.
If you have any issues then contact us and we’ll try to help as soon as we can.
FreeRADIUS FAQ
What is FreeRADIUS used for?
FreeRADIUS is an open-source implementation of the RADIUS protocol server that is mainly used to authenticate various types of network access.
FreeRADIUS provides protocols for:
- Authorisation
- Authentication
- Accounting
What is a RADIUS server and how does it work?
RADIUS is short for Remote Authentication Dial-in User Service. It’s a networking protocol that provides AAA (authorisation, authentication, and account) management protocols. The radius server works on the application layer and uses TCP/UDP protocols on the transport layer.
What are some RADIUS server use cases?
The RADIUS server is a client/server protocol and software. It enables remote access servers to communicate with a central server in order to authenticate users and authorize their access to the requested server or network.
Bài viết gốc: https://bytexd.com/freeradius-centos/

Nhận xét
Đăng nhận xét